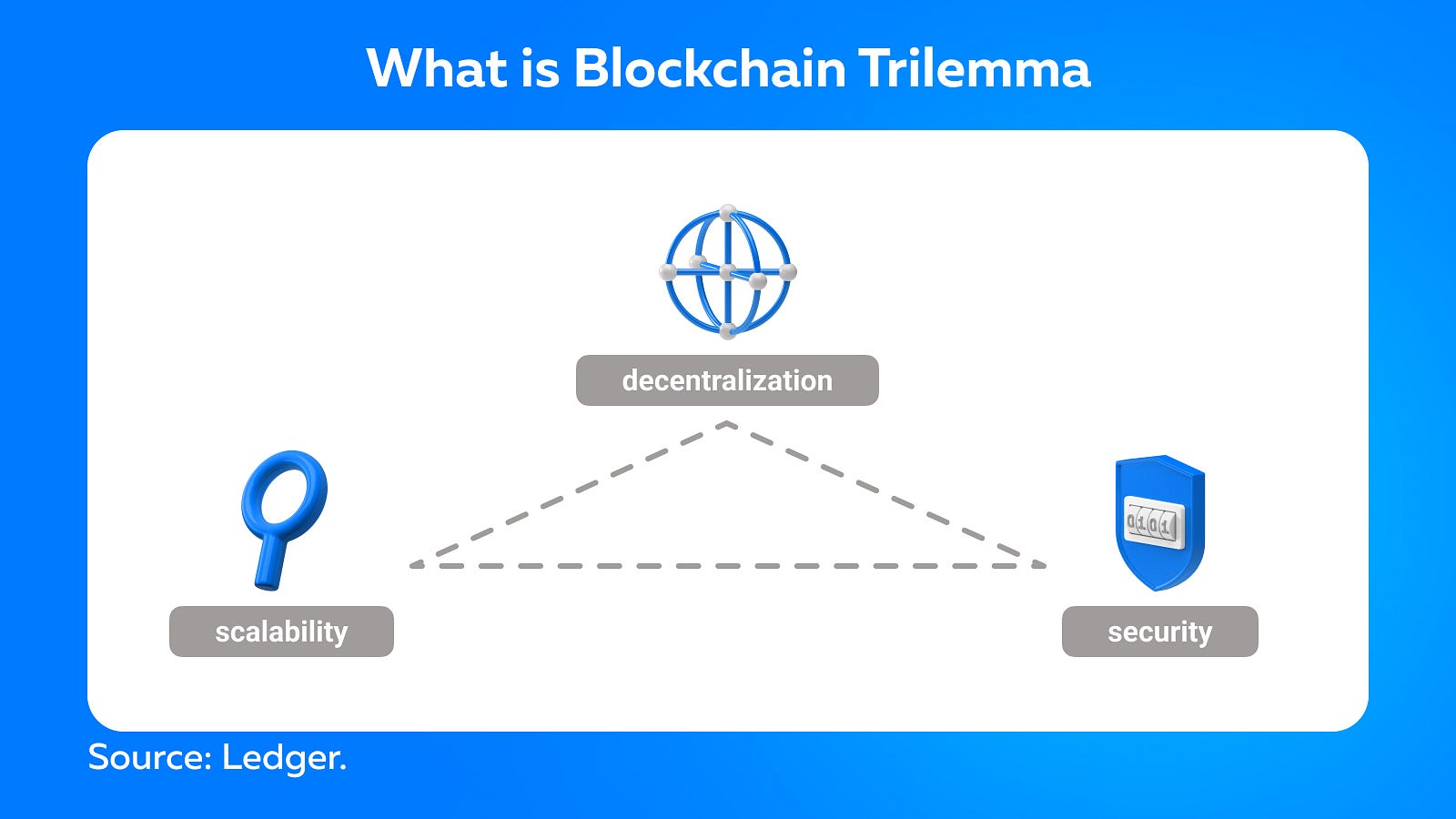
Blockchain technology has indeed established itself as a new pillar of the global economy. However, it faces a unique challenge known as the blockchain trilemma, which is to balance decentralization, security, and scalability in its infrastructure.
Decentralization refers to a network’s meaningful distribution of computing power and consensus, while security refers to protection against attacks. Both are considered non-negotiable for proper functioning. Another important feature of blockchains is scalability, which is the ability to support high transaction throughput and enable future growth. Scalability is crucial because it is the only way for blockchain networks to compete with legacy centralized platforms.
For instance, Bitcoin currently processes between 4 and 7 transactions per second, while Visa, at the same time, can handle thousands of transactions. Blockchain technology must meet or exceed these high levels of scalability in order to compete with existing payment systems.
Thanks to a whole new generation of blockchain platforms and scaling solutions designed specifically to address the problem of scalability, we’re making exponential progress toward a world where blockchains can handle the transaction throughput required for widespread adoption. Let’s look at Layer-1 and Layer-2 solutions.
What Are Layer-1 and Layer-2 in Cryptocurrency?
A Layer-1 network refers to the blockchain itself, while a Layer-2 protocol is an integration that can be used alongside a Layer-1 blockchain. Examples of Layer-1 blockchains are Bitcoin, Litecoin, and Ethereum. Lightning Network is a sample of a Layer-2 protocol.
Layer-1 Scalability Solutions
Layer-1 solutions increase throughput and transaction speed by changing protocol rules, allowing for more users and data. The first layer of scaling solutions may include, for example, increasing the amount of data contained in each block or increasing the block confirmation rate. Currently, several methodologies are being developed to improve the scalability of blockchain networks:
- Consensus protocol improvements
Some consensus algorithms are more efficient than others. Proof of Work (PoW), for example, is a popular consensus protocol used in blockchain networks such as Bitcoin. In PoW, computers must compete to solve complex mathematical puzzles in order to add new transactions to the distributed ledger. Despite its security, PoW can be very slow.
This is why many emerging blockchain networks favor the Proof-of-Stake (PoS) consensus mechanism. Rather than using significant computing power to solve cryptographic algorithms, PoS systems process and validate new blocks of transaction data based on participants placing collateral on the network.
One of the well-known examples is Ethereum’s attempt to move from PoW to a PoS consensus algorithm. The expected result is a dramatic increase in network capacity without sacrificing security or decentralization.
- Sharding
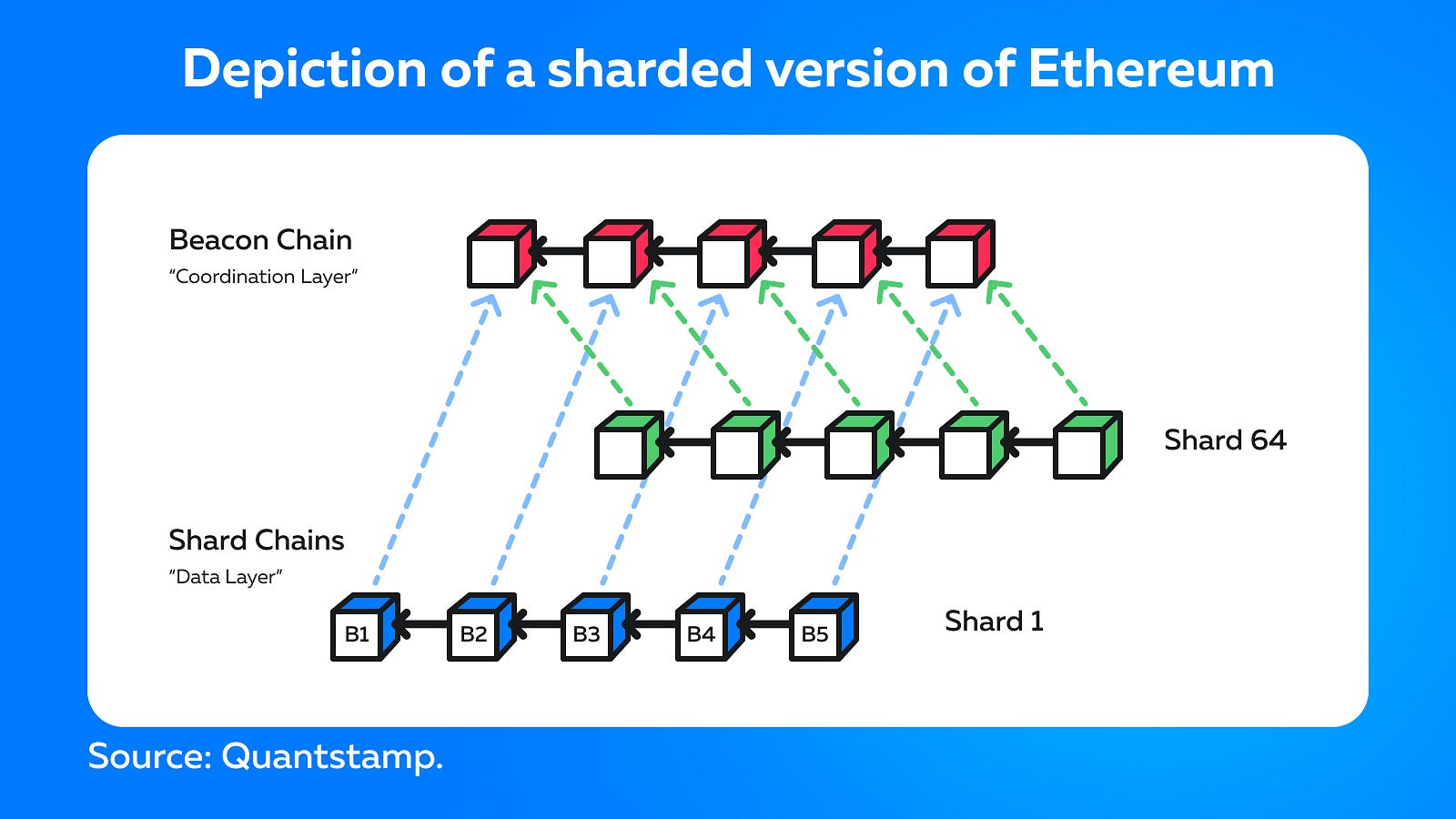
Sharding is a method of partitioning and storing a single logical set of data across multiple databases. It’s one of the most popular Layer-1 scaling solutions in the blockchain sector. The concept of sharding has been used in traditional centralized database management since the late 1990s. The term “shard” (fragment) gained popularity thanks to one of the first massively multiplayer online role-playing games, Ultima Online, in which developers distributed players across different servers (different “worlds” in the game) to cope with traffic.
Sharding is a process that divides the blockchain network into different sets of data, called shards. This task is easier to manage than requiring all nodes in the network to support the entire chain. Transactions can be processed simultaneously by multiple segments of the network, allowing you to work sequentially with numerous transactions. Additionally, each node is assigned to a specific shard instead of having to store the entire blockchain. Individual shards provide proof to the main chain and communicate with each other to exchange addresses, balances, and shared states.
Zilliqa is the first platform to introduce sharding. At the testnet stage, it managed to reach 2,828 transactions per second. In turn, the Near blockchain ecosystem allows developers to create and use decentralized applications. Near calls itself a “PoS sharded blockchain” and claims its sharding technology allows nodes to remain small enough to run on low-end devices — potentially even mobile phones. Ethereum 2.0 explores shards along with other blockchains such as Zilliqa, Tezos, and Qtum.
Layer-2 Scalability Solutions
Layer-2 solutions refer to a network or technology built on top of the underlying blockchain protocol. This type of scalable solution transfers some of the burden of processing transactions to the neighboring system architecture, which then handles most of the network processing and only subsequently reports back to the main blockchain to complete its results. By shifting most of the data processing to a supporting platform, the base layer blockchain becomes less congested and ultimately more scalable. Examples of Layer-2 solutions include:
- Nested Blockchains
A nested blockchain runs on top of another blockchain. With this scheme of work, Layer-1 sets the parameters, and the Layer-2 nested blockchain executes the processes.
The main blockchain can have several levels. This is easy to visualize based on a typical company structure. The manager receives work tasks, then assigns them to subordinates, that later report to the manager on the completion of the assigned tasks. Thus, the load on the manager is reduced, and scalability is increased.
Multiple layers of a blockchain can be built on the main chain, with each layer using a parent-child connection. Parent chain delegates operate on child chains that process data and return the parent chain when completed. The underlying blockchain does not participate in the network functions of secondary chains unless dispute resolution is required. Distributing work throughout the network reduces the burden on the main chain, making it exponentially scalable.
One example of a layer-2 blockchain infrastructure that operates on top of the Ethereum protocol is the OmiseGO Plasma project.

- State Channels
State channels create two-way communication between the blockchain and off-chain transaction channels, thus improving the overall throughput and speed of transactions. State channels do not require verification by Layer-1 network nodes. They represent a resource adjacent to the network that is isolated using a multi-signature mechanism or a smart contract.
When a transaction or batch of transactions is completed in a state channel, the final “state” of the “channel” and all transitions inherent in it is recorded on the underlying block chain. State channels sacrifice some degree of decentralization in order to achieve greater scalability.
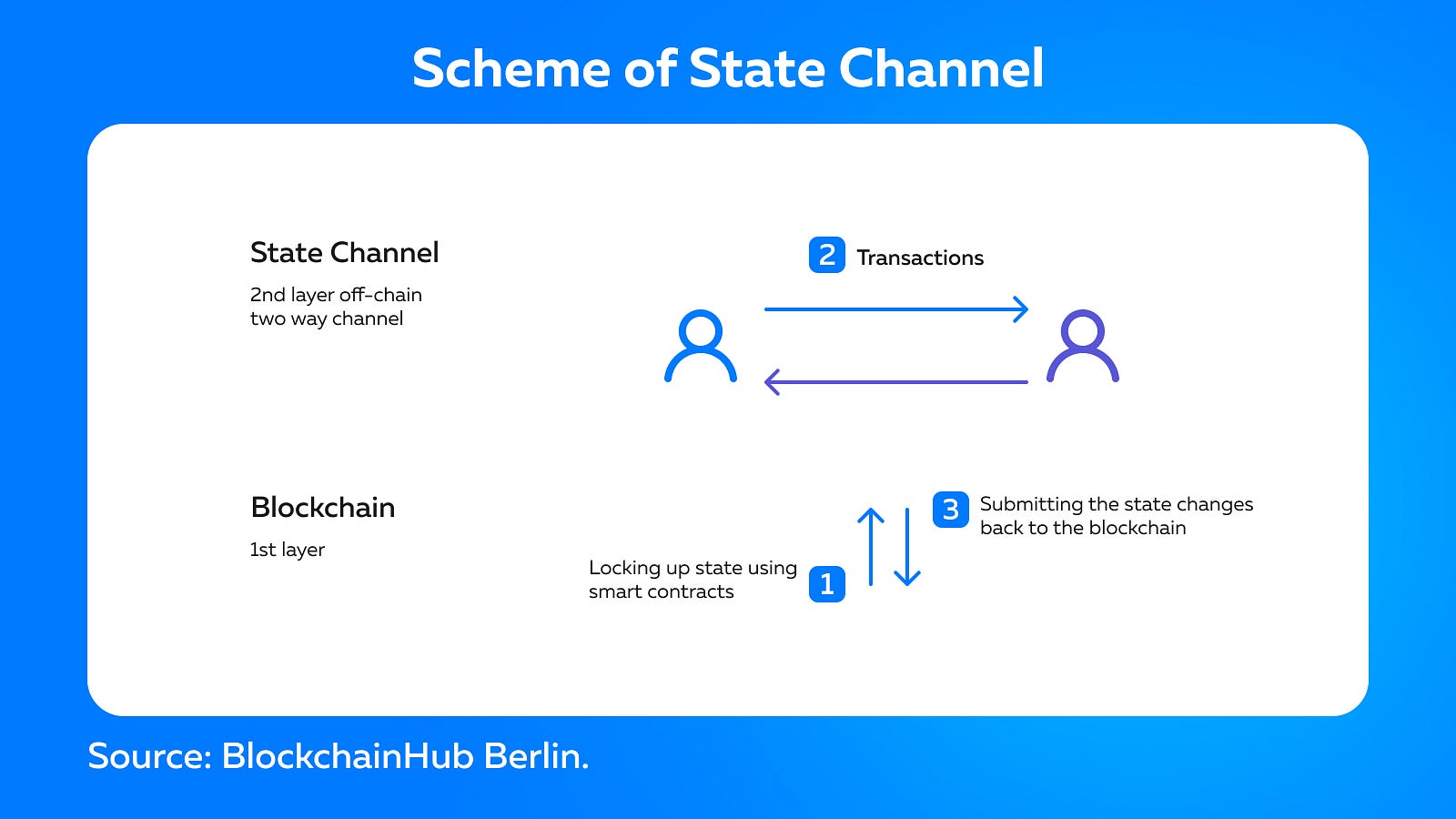
Examples of State Channels: Bitcoin Lightning, Liquid Network, Celer, Raiden Network.
- Sidechain
A sidechain is a separate block chain that is attached to a parent chain using a two-way peg. It is a transaction chain that facilitates a large number of transactions. It has a consensus mechanism independent of the native layer. This mechanism can be optimized to improve scalability and processing speed.
When using a sidechain, the main blockchain must confirm transaction records, provide security, and resolve disputes. Sidechenes differ from state channels in that they publicly record all transactions in a ledger. In addition, if a security breach occurs on a sidechain, it does not affect other sidechains or the main base layer blockchain.

Let’s look at the simple process of sending cryptocurrency to another user in the sidechain:
- Sending
The user sends coins to a specific address, where they become inaccessible to the original owner.
2. Waiting for Confirmation
The asset transfer can be completed, but the user needs to wait for official approval. The process may take a certain amount of time, but it is necessary to protect assets.
3. The use of a new sidechain.
After confirmation, the coins are issued to the sidechain. Their sum is equal to the original sum. From this moment, the user can work with the assets.
Examples of Sidechains: Plasma, Polkadot, Rootstock (RSK), Ardor, Loom.
- Rollups
Rollups are designed to reduce gas fees by compressing the amount of data in Layer-1 blockchains. Rollups are Layer-2 blockchain scaling solutions that execute transactions outside the Layer-1 blockchain and place data on completed transactions on it. The data is at the base layer, which allows Layer-1 to keep rollups secure.
Rollups are built on two security models:
Optimistic rollups
Instead of verifying each transaction at Layer-2, the main network simply broadcasts them and “optimistically” assumes they are legitimate unless disputed by anyone. Calculations occur only when fraud is proven.
Optimistic Rollups can offer scalability improvements because they don’t perform any calculations by default. For instance, on the Ethereum blockchain, computing is slow and expensive. In this case, Optimistic Rollups can offer up to 10–100x scalability improvements.
Anyone can become a validator and check if someone is trying to cheat. Validators monitor cases of opening disputes. Users who are not validators can only become victims of fraud if all 100% of the validators are in cahoots. Later-2 is safe as long as there is at least one honest validator on the network. Moreover, the network will be secure even if all the validators are saboteurs but are not in cahoots to consistently lie.
When the act of fraud is proven, the rogue validator is slashed and loses the deposit. This motivates network members to behave honestly and makes sabotage unprofitable.
Examples of Optimistic rollups: Optimism Ethereum, Arbitrum, Boba Network.
Zero-Knowledge rollups
ZK-Rollup combines hundreds of off-chain transactions and generates a zero-knowledge cryptographic proof known as SNARK, which allows one party to prove that they have certain information without exposing that information. This feature provides a high level of privacy in public blockchains.
ZK-SNARK is used to verify each block added to the network, eliminating the need to trust the validators. While the Optimistic Rollups solution is based on the fact that all validators are honest, ZK-Rollups checks their honesty using the ZK-SNARK mathematical proof. All transactions go through at Layer-2, and ZK-SNARK is hosted at Layer-1. It turns out that ZK-Rollup does not need to rely on the integrity of the validators, and the security of the external network has the same level as the security of the base network, for instance, the Ethereum blockchain.
In ZK-Rollup, there are no delays in withdrawing funds from Layer-2 to Layer-1 since the proof of validity accepted by the ZK-rollup contract has already confirmed the funds. Unlike Optimistic Rollups, there is no fraud check required, which can delay withdrawals by up to two weeks.
ZK-Rollups has another opportunity to reduce the commission. The more people use this technology for transactions, the cheaper the transaction can cost each of them. ZK-Rollups can combine any number of transfers in one data package. When such a package gets back into the blockchain, you need to pay for one action. This commission is shared among everyone whose transactions were in the batch. As a result, the more operations get into the data package, the less each user should pay.

Examples of Zero-Knowledge Rollups: Loopring, zkSync, Snark.
Further thoughts
Blockchain layering has several advantages. The main benefit of Layer-1 solutions is that developers don’t have to add anything to the existing architecture since only the base layer changes.
Layer-2 scaling decisions, in turn, do not affect the underlying protocol. In addition, these solutions allow you to perform multiple microtransactions, and users do not need to pay sky-high transaction fees or spend time on verification from the miner.
However, both of these blockchain layers have limitations that need to be taken into account. The main question is, will Layer-1 NAd Layer-2 blockchain scaling solutions be temporary or permanent? Let’s see what the future holds for blockchain technology!
